The Saturday morning following the deadly terrorists attacks in Paris, the hacktivist network Anonymous declared war on ISIS. In a widely distributed video, a figure in a Guy Fawkes mask announced Operation Paris, or #OpParis, and promised the Islamist group that “Anonymous from all over the world will hunt you down.”
So far, Anonymous’ much-hyped digital war has generated lots of headlines but not much in the way of impressive results. It’s been mostly focused on identifying ISIS-affiliated websites, Twitter accounts, and internet addresses and reporting them to Twitter and other webmasters in an effort to get them shut down. Shortly after OpParis launched, Anonymous claimed to have helped get 5,500 ISIS Twitter accounts taken down, a number that ballooned to 20,000 by last Friday. An unnamed Twitter spokesperson told the Daily Dot that Anonymous’s claims are “wildly inaccurate.”
“In terms of effectiveness, I think all they can do is make a small dent,” says Gabriella Coleman, an anthropologist and the author of Hacker, Hoaxer, Whistleblower, Spy: The Many Faces of Anonymous. “Since they started, ISIS’s online presence hasn’t really shrunk or grown. It doesn’t really matter if there is a small dent. ISIS, unlike Al Qaeda, has been really savvy with online propaganda.” Last week, ISIS posted a message on the encrypted messaging app Telegram, calling the hacktivists “idiots” and offered an online security guide for their sympathizers. Noting that Anonymous had only gone after Twitter accounts, the message joked, “What they gonna hack?”
And “Anons” themselves are riven by questions about whether OpParis can really deliver its promised punch. Anonymous’ recent efforts to dox Ku Klux Klan members also fingered people with no ties to the hate group. And the anti-ISIS campaign has already faced similar verification problems, exposing people who have no connection to the militant group, prompting a hacker known as the Jester to pen a blog post critiquing Anonymous’ efforts as “a comedy of errors.” OpParis responded in a Tweet that has since been deleted:
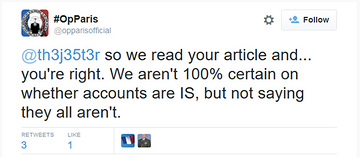
@opparisofficial Little late now isn’t it? Media praising u for naming these ppl as ISIS & ur like, well actually only ‘some’ *might* be.
— JΞSTΞR ? ΔCTUAL³³º¹ (@th3j35t3r) November 18, 2015
In an open letter, an Anon called Discordian writes that Operation Paris “has nothing to do with stopping ISIS…It’s about stroking the ego of Anonymous in a desperate attempt to be relevant.” Discordian goes on: “How exactly do they plan to stop an international terrorist organization that has been able to plot attacks regardless of the mass-spying by governments around the globe? Taking down their communications may disrupt valuable intelligence that can be used to track down these terrorists.”
Concern that Anonymous is potentially hindering rather than helping official counterterrorism efforts is one of the motivations behind Ghost Security Group, a collection of self-described ex-military personnel and computer security experts that splintered from Anonymous. Ghost Security Group, formerly GhostSec, now rejects the Anonymous model, in which anyone taking up the group’s banner may act in its name, regardless of experience or intentions. “I’ve seen innocent Muslim sites being attacked, mistaken for being an ISIS site,” as a result of Anonymous’ activity, says a Ghost Security Group member who asks to be called DigitaShadow.
“Their intentions are good, but the way they operate—decentralized, everybody does what they want and they all have different ideas, it makes it difficult. The government doesn’t want to work with Anonymous,” says DigitaShadow. Unlike Anonymous, Ghost Security Group says it cooperates with American officials so it does not get in the way of active terrorism investigations. In the wake of the Paris attacks, Ghost Security Group has been collecting Telegram channels and identifying social-media accounts and sending them to US authorities, says DigitaShadow.
According to DigitaShadow, Ghost Security Group members in the United States, Europe, and the Middle East monitor social media and infiltrate online forums and Telegram channels to uncover intelligence on ISIS’s recruitment as well as specific threats. He says Arabic speakers vet Ghost Security Group’s targets to avoid mistakes. Through a combination of reporting ISIS-linked social-media accounts and distributed denial of service attacks, Ghost Security Group claims to have taken down 149 ISIS-affiliated websites, 110,000 social-media feeds, and 6,000 videos since January. (Anonymous members who still fly the GhostSec flag dispute these numbers, saying that at least half of these actions occurred when the entire group was still affiliated with Anonymous.)
Ghost Security Group sends its findings on to Michael S. Smith II, an intermediary who says he passes the information onto US counterterrorism officials. Smith, co-founder of the security firm Kronos Advisory, tells me that his relationship with Ghost Security Group dates back to July, when the group forwarded him details about a potential terror plot in Tunisia. Ghost Security Group had uncovered information indicating that ISIS was planning to target tourists at a beach resort where an ISIS-linked militant armed with an AK-47 had gunned down 38 people just weeks earlier. It was the kind of attack, says Smith, that “would have looked like what happened in Paris, or similar to what occurred in Mumbai.”
Smith says he took that information and handed it to federal officials. Days later, more than a dozen suspects were arrested by Tunisian police. “I received explicit feedback from the officials whom I passed the information on to that the information was indeed utilized to help with that interdiction activity,” Smith says. While Ghost Security Group’s efforts speak to a more professional and effective organization, no government officials have publicly acknowledged the group’s efforts. And Smith would not name any of the officials he has ties to.
Some Anons take issue with the idea of assisting Western governments, even to combat a common enemy. “It seems rather foolish to me to be aiding our mortal enemies, who lock up and even torture Anons—in a fight against an evil that they themselves actually created,” said a hacker called X in an interview with Tech Insider. “If the USA and Europe were willing to release our Anon POW’s, and agree to stop attacking us in exchange for our rather ample assistance against ISIS, well that might be different.”
This discomfort with hacktivists building ties to officialdom has prompted some Anonymous members to scrutinize Ghost Security Group’s relationship with the US government. One of them is @blackplans, who tells me via direct message on Twitter that he has been under the Anonymous banner for “more than a few years.” He believes that the people behind Ghost Security Group are either taking government money or have been forced to work with the feds.
As evidence of this theory, @blackplans cites a 2014 Joint Cyber Bulletin from the California State Threat Assessment Center and two other security agencies that describes DigitaShadow as an Anonymous-affiliated “malicious cyber actor” who targeted law enforcement and government websites, and doxed two government officials. “For him to now claim he works with the feds seems mighty odd,” says @blackplans. Ghost Security Group, in a statement sent via Twitter, says, “We receive funding from our supporters only. We are not funded by any government agency whatsoever.”
Yet @blackplans also has little trust in those behind Operation Paris or Operation ISIS, which began in January in response to the Charlie Hebdo killings. On Twitter, he highlighted Operation ISIS’s call for financial contributions. “See here’s the kind of thing that makes me want to avoid #OpISIS, #OpIceISIS & #OpParis. Who is behind the curtain?” he wrote. In a direct message, he noted, “Any time money and shady motives have ever touched an Anonymous op or grouping, they are permanently damaged or tainted by that association.”
A lack of accountability has long been one of the main criticisms of Anonymous, which raises the question of just how effective online vigilantes can be in fighting an enemy like ISIS. For now, the hacker war on ISIS seems to be generating more self-aggrandizing PR than actual damage.
This article has been updated.
















